← All Tutorials
NIS2: Backup and Cyber Resilience with Iperius
NIS2 Directive Compliance: Backup and Cyber Resilience with Iperius

For those in a hurry
- The NIS2 Directive imposes stringent cybersecurity requirements : Business Continuity/Disaster Recovery plans , backup management with redundancy and crisis management are mandatory. At stake are fines of up to 10 million euros or 2% of turnover for essential companies, in addition to possible personal liability of managers.
- Backup and operational resilience are central : NIS2 requires secure, offline and geographically distant backup copies from the main site, with adequate encryption and access control . The goal is to ensure operational continuity even under attack (ransomware, data breach, etc.) and minimize data loss and machine downtime.
- Iperius Backup Suite: key solution for NIS2 compliance : supports hybrid and multi-cloud backups (local, NAS, public and private clouds), immutable backups (Object Lock on S3, WORM on tape, air-gapped backups ), applies the 3-2-1 rule (redundant copies even off-site), performs disk images and automatic VM and database backups for rapid disaster recovery. All with AES 256-bit encryption , standard formats (no vendor lock-in) and cloud storage plans on ISO 27001 certified European data centers .
- Proactive security and reduced costs : Iperius offers a centralized console to monitor backup and IT security in real time, perpetual licenses (no annual fees) and a low TCO to facilitate compliance with NIS2. The result is greater resilience against ransomware and advanced threats, ensuring business continuity and regulatory compliance.
Download and try Iperius Backup now
NIS2: New EU obligations on cybersecurity and business continuity
The new NIS2 (Network and Information Security 2) Directive represents a quantum leap in European cybersecurity regulations. Effective from 2024, it requires a broad spectrum of companies (not only critical infrastructures but also many industrial sectors and ICT suppliers) to adopt rigorous cybersecurity measures . The aim is to ensure a high common level of protection against cyber attacks throughout the European Union.
Key provisions of NIS2 include: the implementation of effective Cybersecurity Risk Management , technical and organizational security measures (e.g. access control, network monitoring, incident response plans), timely incident notification (within 24 hours an initial notification, detailed reporting within 72 hours) and supply chain management . Furthermore, the Directive introduces strong accountability of top management : managers can be held directly liable in case of non-compliance, with heavy fines and even suspension of activities in serious cases. For “Essential Entities” (e.g. energy, transport, healthcare, finance) fines can reach 10 million euros or 2% of annual turnover, and up to 7 million or 1.4% for other important entities.
Business continuity and resilience are key principles of NIS2. The regulation requires that organizations develop and maintain a Business Continuity Plan (BCP) and Disaster Recovery (DR) plan, to be implemented in the event of cyber incidents. This plan, based on a risk assessment, must define roles, emergency procedures, recovery priorities and necessary resources (including backups and redundant systems). In parallel, NIS2 requires the preparation of a cyber crisis management plan , with dedicated teams and procedures to respond in a coordinated manner to high-severity incidents (for example, attacks that compromise business continuity, data or reputation).
Backup and Data Protection: A Must-Have for NIS2
At the heart of the NIS2 Directive is the recognition that disaster recovery and backup are not optional extras, but essential components of business resilience. The regulation explicitly requires entities to maintain backup copies of data , with sufficient resources and infrastructure to ensure an adequate level of redundancy . In practice, this means adopting robust backup strategies that ensure critical data is duplicated and safe in multiple locations , ready for recovery when the need arises.
NIS2 requires backup plans to include specific parameters: acceptable recovery time (RTO) must be defined , the completeness and integrity of copies must be regularly verified (even for cloud data), and – crucially – offline or off-site backups must be maintained in secure locations, outside the main network and sufficiently distant geographically from the primary site. This approach ensures that, in the event of a physical disaster or targeted attack (such as ransomware), intact copies of data exist that are isolated from the event. Furthermore, the Directive requires that such backups be protected by robust security measures , including data encryption and tight controls on physical and logical access to the copies. Finally, emphasis is placed on recoverability : organizations must periodically test recovery from backups and ensure that data can actually be restored within the established objectives. In short, backup, redundancy and recovery times become compliance KPIs.
These measures are not just bureaucracy, but respond to real threats. Ransomware , in particular, is cited as a cause of the increase in serious incidents: in 2023, there was a 50% increase in ransomware attacks in the first half of the year. Such attacks can paralyze a company, encrypting servers and critical data. Without a valid backup, the alternative is to pay exorbitant ransoms with an uncertain outcome. Suffice it to say that, according to statistics, over a third of organizations suffer from ransomware every year , and of these, around 32% end up paying a ransom – but on average only recovering 65% of the stolen data. Even more worryingly, only 57% of victims manage to mitigate the attack by restoring data from backups . This means that almost half of the affected companies did not have sufficiently robust or recent backups, or were unable to use them for a full recovery. Data loss and prolonged operational disruption are among the most serious consequences of these scenarios.
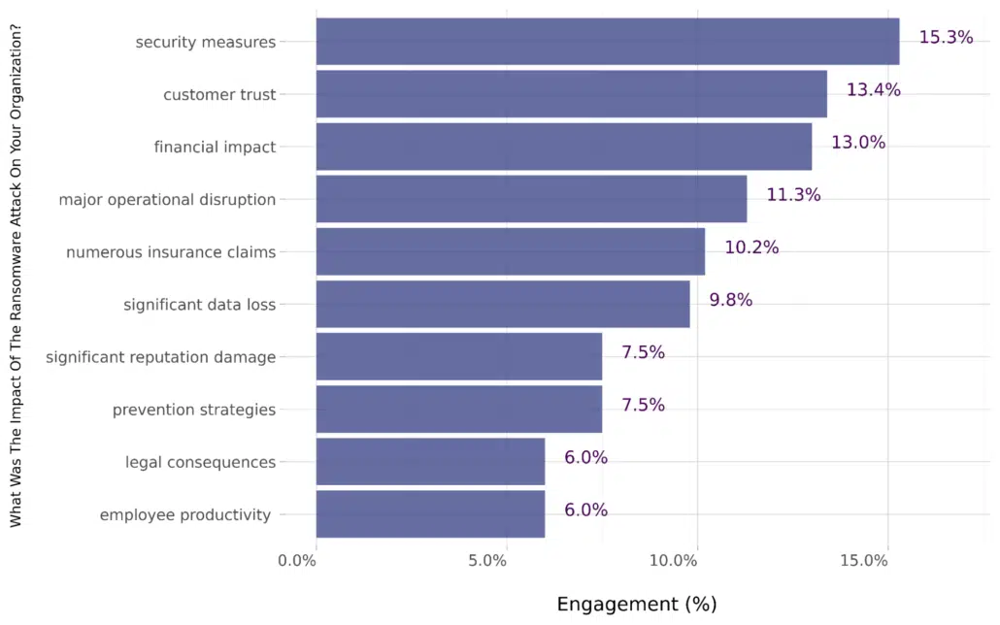
Impact of a ransomware attack according to a 2024 survey: in addition to necessary security upgrades (15%), companies report impacts on customer trust (13%), financial losses (13%) and significant data loss (9.8%) , resulting in operational and reputational damage.
In light of this, compliance with NIS2 goes hand in hand with the adoption of backup and disaster recovery best practices . For example, the 3-2-1 rule is highly recommended : keep 3 copies of the data (the original plus two backups), on 2 different media (e.g. local disk and cloud) of which at least 1 off-site . This multi-copy strategy ensures that a single event cannot compromise all copies of the data. At the same time, backup resilience must be pursued : keep at least one immutable (not alterable or erasable) and/or offline copy ; apply strong encryption (e.g. AES 256 bit) to prevent unauthorized access; and constantly monitor the status of the backups. In essence, backup = security : it is one of the most effective defenses against ransomware and disasters, and NIS2 elevates it to a regulatory requirement.
Iperius and NIS2: all the solutions for compliance and business continuity
How can we translate NIS2 requirements into concrete actions? Iperius Backup – the complete suite of backup and data protection products from Enter Srl – represents an effective and immediate response. Thanks to a set of advanced features, Iperius helps companies meet legal obligations while strengthening their IT resilience . Below we examine the main technical and strategic advantages offered by Iperius from a NIS2 perspective.
➤ Hybrid and multi-cloud backups on secure services: Iperius natively supports flexible backup strategies, combining on-premises and cloud destinations . Data can be saved simultaneously on local storage (disks, NAS, SAN), network drives, as well as on public clouds (such as Amazon S3, Microsoft Azure, Google Drive) and private or proprietary clouds. This hybrid architecture allows you to easily implement the 3-2-1 rule , keeping copies in physically separate locations. For example, a company backup can reside on a local NAS for rapid restores and operational recovery , and at the same time on a secure cloud datacenter to deal with disasters on the main site. All transfers to the cloud take place via encrypted connections (HTTPS/SSL) and on services with high security standards and geographic redundancy , ensuring that the remote copy is always available and protected. From a NIS2 perspective, this means automated and compliant off-site backups , without having to rely on manual processes. Critical data remains safe even in the event of fire, flood or theft at the local office, satisfying the requirement to keep copies in secure, remote locations .
➤ Immutable and air-gapped backups (Amazon S3 Object Lock, Tape WORM): One of the most appreciated features of Iperius is the ability to create tamper-proof backups . The suite supports Amazon S3 Object Lock , which allows you to make objects saved in the bucket immutable for a defined period of time: no one, not even an administrator, will be able to modify or delete them during that period of time. This is a very powerful antidote against the most aggressive ransomware, which often tries to delete or encrypt backups as well. In parallel, Iperius offers native support for tape drives (LTO) including WORM (Write Once Read Many) mode : data written to WORM tapes cannot be altered or overwritten, ensuring permanent and non-erasable copies . Furthermore, the Iperius strategy can be configured to create “air-gapped” backups , that is, stored offline or in any case isolated from the network (for example on removable drives disconnected after the backup, or on tapes stored off-site). These techniques concretely implement what is required by NIS2 in terms of backup protection: having copies inaccessible to attackers , even if the company network is compromised. An immutable/offline backup guarantees that, whatever happens to the production system, there will always be an intact copy of the data to start from. Anti-ransomware resilience means exactly this: eliminating every “single point of failure” and preventing malware from having the last word.
➤ 3-2-1 backup strategy and guaranteed redundancy: Iperius encourages and simplifies the adoption of the 3-2-1 best practice. Its flexibility of destinations allows you to easily maintain three copies of the data on different media. For example, with a single Iperius backup plan you can create a local copy (e.g. USB disk), a copy on network storage and one on the cloud, all in parallel. In addition, the software allows versioning and advanced retention: you can keep multiple historical versions of the files, avoiding overwriting the good copies with corrupted or encrypted files. These features respond perfectly to the NIS2 dictate of having complete and correct backups, with adequate redundancy . In addition, Iperius allows you to verify the integrity of the backups (thanks to detailed logs, checksums, and the possibility of periodic test restores using the integrated restore functions). This helps to document the results of the tests and highlight any problems, as required by the legislation. In short, with Iperius implementing a solid 3-2-1 policy is not a burden but an automated, monitored process tailored to your needs.
➤ Disk Image and instant disaster recovery of virtual machines: In the event of a serious incident, recovery speed is everything. Iperius offers advanced disk image and virtual machine backup capabilities , which are essential for Business Continuity . The Iperius Disk Image module allows you to create a complete image ( block-level ) of the entire system, including the operating system, applications, configurations and data. This image can be duplicated on multiple destinations (including cloud) and allows for rapid bare-metal restore : in the event of a total server failure, the entire system can be restored to new hardware (even different) in a very short time, minimizing downtime. Similarly, Iperius is compatible with the most popular virtualized environments (VMware vSphere, Microsoft Hyper-V, Proxmox, etc.): it is able to perform automatic hot backups of VMs , without interrupting services, and to quickly restore virtual machines both on-site and on alternative hosts. Iperius also supports forever-incremental replication of VMware virtual machines. This means that, for example, if ransomware hits a server, you can start the reserve VM on another host, restoring the service in a few minutes ( Instant VM Recovery feature ). In the case of a backup, restoring a VM is still very quick and allows you to get back up and running with just a few simple steps. These disaster recovery capabilities directly respond to the NIS2 needs to ensure business continuity: the Business Continuity Plan can count on very low RTO and RPO thanks to Iperius image backups and VM replicas. In practice, not only is the data safe, but entire critical infrastructures can be quickly put back on their feet, limiting the impact of any incident.
➤ Compressed and encrypted backups (AES 256 bit): The security of backup data should not be overlooked – after all, a flaw in the reserve copies would nullify the usefulness of the backup itself. For this reason, Iperius integrates advanced AES 256-bit encryption mechanisms on backup files. The user can set a password so that each backup is encrypted with a strong-key symmetric algorithm: in the event of unauthorized access to the media (e.g. a stolen disk or cloud account), the data remains unreadable. This contributes to NIS2 compliance, which requires protecting backups with adequate measures including the use of encryption . At the same time, Iperius compresses the data (standard Zip format) optimizing the space occupied and the transfer speed, without ever sacrificing integrity. The combined use of compression and encryption makes backups leaner and more secure : the impact on the network and storage is minimized, and confidentiality is protected even in the public cloud. It is worth noting that Iperius encryption is optional and granularly configurable: the company can decide which data to encrypt (for example, only sensitive or GDPR-compliant data) and manage the keys in-house. In any case, implementing an end-to-end encryption policy for backups significantly increases the overall security level, reducing the risk of data breaches even in extreme scenarios.
➤ No vendor lock-in (standard and accessible formats): Unlike some enterprise solutions that use proprietary formats that are difficult to read without the original software, Iperius adopts standard or documented saving formats , ensuring data portability . For example, file-level backups can be generated as zip archives that can be opened with any utility, or as mirror copies on a file system. Virtual machine backups are obtained as standard VMDK/VHD/VHDX files , just as Iperius disk images can be mounted as virtual disks. This means that data saved with Iperius always remains recoverable , even without Iperius itself. In audit or emergency contexts, you are not tied to a specific vendor to access your backups . This “open” approach facilitates business continuity and compliance: for example, if tomorrow the company decides to migrate the data to another platform, Iperius backups will not represent an obstacle. Furthermore, the absence of lock-in is advantageous for NIS2 purposes because it avoids critical dependencies on third parties: the Directive emphasizes risk assessment throughout the ICT supply chain , and having your data stored in an accessible format mitigates the risk of backup inaccessibility due to supplier issues (e.g. termination of service or vulnerabilities in the backup software itself).
➤ Cloud Storage with certified European data centers (GDPR and ISO 27001): For organizations that want an integrated cloud solution, Iperius offers Iperius Cloud Storage with servers located in Europe (specifically in Italy) at ISO/IEC 27001 certified data centers. This ensures that data sent to the cloud fully complies with data sovereignty and GDPR compliance requirements , as well as benefiting from the highest physical and logical security standards.
An ISO 27001 certified data center ensures rigorous information security management processes, access controls, 24/7 monitoring and verified business continuity plans – elements perfectly in line with NIS2’s intent to strengthen the entire digital supply chain. By using the Iperius cloud, companies have certainty about the location of their backups (no data stored outside the EU) and their protection against threats and failures. Furthermore, Iperius Cloud natively implements redundancy on multiple nodes and replicated storage, adding an additional level of resilience . In a NIS2 scenario, this means being able to use the cloud for off-site copies with the peace of mind of being compliant with both European cybersecurity and personal data protection regulations. It’s a double advantage: security and compliance by design .
➤ RMM Console for remote security monitoring (backup, antivirus, etc.): The Iperius suite also includes a powerful centralized console ( Iperius Console ) with RMM ( Remote Monitoring & Management ) functionality. From a single dashboard, accessible via the web, the IT manager can monitor in real time all the backups in progress on the various devices, check the outcome of the scheduling, receive immediate alerts in case of errors or problems (also via the dedicated app) and generate periodic reports on the status of the protections. But not only that: the console also allows you to keep an eye on other aspects of endpoint security, integrating for example the control of the antivirus and firewall.
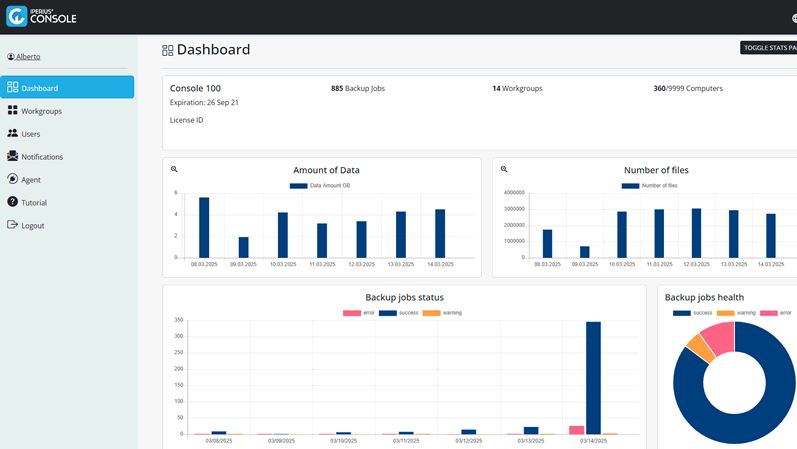
This tool is crucial to ensure the continuous visibility required by NIS2: the regulation in fact requires constant monitoring of defenses and a rapid response capacity to incidents. Thanks to Iperius Console, the company can implement a true 24/7 presence on its backups and systems , with notifications that allow immediate intervention if something goes wrong (for example, a failed backup or running out of disk space). Furthermore, the console acts as a control center for compliance : you can easily document the backup policies implemented, the timing and even remotely manage configurations and updates of Iperius clients. From an NIS2 audit perspective, having this centralized supervision greatly facilitates both effective compliance with security SLAs and formal demonstration of what has been done (e.g. reports to be shown in the event of checks by the competent authorities). In short, Iperius Console helps transform backup from a technical process to a governed process , integrated into the corporate security framework.
➤ Perpetual license and reduced compliance costs: Unlike many enterprise solutions that require expensive annual or volumetric subscriptions, Iperius adopts a perpetual license model : you buy it once and you can use it indefinitely. Updates and support can be renewed at very low costs, but the software remains functional without the obligation to renew. This approach has a significant impact on the TCO (Total Cost of Ownership) of the backup solution and, consequently, on the costs of adapting to NIS2. Many SMEs fear that compliance with the new regulations will involve expensive expenses; Iperius instead allows you to implement all the required backup measures without excessively weighing on the IT budget . Even the most advanced editions of Iperius (which include functions such as cloud backup, tape backup, immutability, centralized console, etc.) are offered at affordable prices compared to the competition, and above all without recurring fees . This means that even the smallest organizations or those with limited resources can equip themselves with the tools to be compliant with NIS2, with only the initial investment. It is worth noting that, according to some studies, economic and technical obstacles are among the reasons why many companies risk not meeting NIS2 deadlines. By choosing Iperius, this obstacle is significantly lowered: compliance becomes an achievable goal without costly infrastructure revolutions. In addition, the absence of lock-in (as seen above) avoids hidden future migration or exit costs. Click here to see Iperius Backup prices .
➤ Greater resilience against ransomware and advanced threats: Adding up all the above points, the final benefit is clear: with Iperius, the company becomes more resilient . A ransomware attack today no longer represents an existential catastrophe, but a manageable inconvenience . Immutable and off-site backups ensure that data cannot be encrypted or destroyed by the attacker; the 3-2-1 strategy guarantees that there is always at least one recoverable copy; encryption protects against the exfiltration of sensitive information ; rapid restores minimize the downtime of essential services. In other words, the organization is able to absorb the impact of a cyber incident and continue to operate almost without interruptions – which is exactly the ultimate goal of NIS2. Other threats are also mitigated: a data breach can be addressed by quickly restoring clean systems and having the certainty of integrity copies (thanks to periodic tests); a human error or application failure that corrupts data can be resolved by recovering previous intact versions (in a granular way, since Iperius supports incremental and differential backups). Business continuity is safeguarded all-round. As evidenced by the data, investing in robust backups drastically reduces the economic and reputational impacts of any cyber attack.
Conclusion
In conclusion, compliance with the NIS2 Directive should not be seen as a mere regulatory obligation, but as an opportunity to truly strengthen your security posture . Implementing solutions like Iperius means protecting your company’s digital assets and ensuring business continuity even in the most critical scenarios. With Iperius, compliance with NIS2 becomes a natural path: not only do you tick the regulatory box, but you adopt a proactive cyber defense strategy that secures the future of your business. It is an investment in operational peace of mind, customer trust, and business longevity – in other words, the very essence of resilient cybersecurity promoted by NIS2.
Download and try Iperius Backup : your best ally for backup and cybersecurity in compliance with the law. Cyber threats evolve, but with the right tools and a strategic vision oriented towards continuity, every company can face them successfully, transforming regulatory compliance into a competitive advantage.
For any questions or doubts regarding this article,
Contact us