← All Tutorials
Cyber Threats 2025: Evolving Attacks, Data Impact, and How to Protect Yourself

The cybersecurity landscape in 2025 has proven more turbulent than ever. Cyberattacks are on the rise: the average weekly number of attacks per organization has more than doubled compared to 2021. At the same time, the variety and complexity of cyber threats has grown, driven in part by the use of new technologies such as artificial intelligence (AI). It’s not just large enterprises that are being affected: small businesses are particularly exposed, with seven times more organizations reporting poor cyber resilience compared to 2022. In this report, we review the key trends of 2025—from ransomware attacks to sophisticated malware, from advanced phishing campaigns to zero-day vulnerabilities—highlighting the impact on data and businesses and underscoring the importance of backups and disaster recovery plans to mitigate risks.
Unstoppable Ransomware
Ransomware remains the most pressing cyber threat of 2025. According to the World Economic Forum, businesses consider ransomware attacks the greatest cyber risk to their operations. European data from ENISA shows that over 81% of analyzed incidents involved ransomware , often accompanied by data theft and extortion (double extortion), while 15% were unencrypted data breaches. The Ransomware-as-a-Service (RaaS) model has further fueled the phenomenon, lowering the barriers to entry for cybercriminals. The result is a constantly growing attack volume: for example, in October 2025 alone, 623 known ransomware attacks were recorded, an increase of over 30% compared to the previous month. Overall, in the first ten months of the year, ransomware attacks increased by 50% compared to the same period in 2024, reaching near-record levels. The affected sectors range from manufacturing to healthcare, from professional services to energy, proving that no sector is immune. A case in point is a British retail giant forced to suspend online services for 15 weeks after an attack, resulting in estimated losses of $300 million.
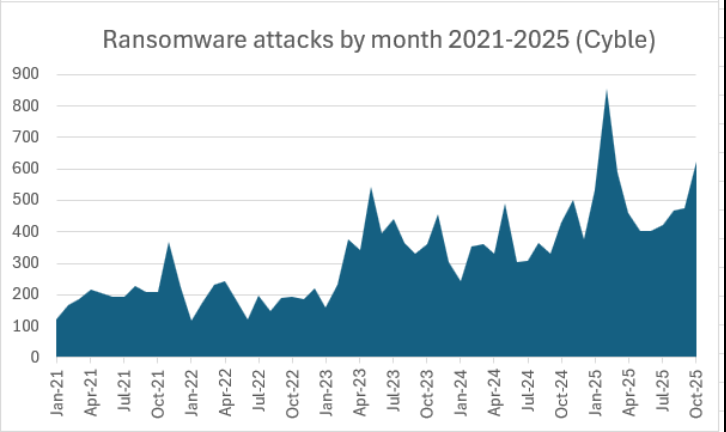
Monthly trend of ransomware attacks (2021–2025) according to Cyble data: the graph shows an escalating trend with a peak of almost 900 attacks in January 2025 and still high levels (>600) at the end of the year.
The professionalization of the criminal ecosystem is a key factor: well-organized ransomware groups collaborate, exchange tools, and leverage automation to maximize their impact. New variants and groups continually emerge, replacing dismantled ones. This cybercrime business model makes ransomware attacks unpredictable and increasingly effective . For victims, in addition to the immediate financial damage resulting from system downtime, there’s the threat of having their stolen data published on the dark web if they refuse to pay the ransom—a lever criminals use to increase pressure. It’s no surprise, then, that double extortion makes data breaches and ransomware two sides of the same coin in this year’s statistics.
Advanced malware and fileless techniques
Alongside the ransomware explosion, 2025 has seen an evolution in traditional malware and the tactics used to compromise systems. On the one hand, the numbers remain impressive: Kaspersky reports that its security systems blocked over 500,000 malicious files every day in 2025, a sign of the breadth of the malware threat in circulation. On the other hand, many attacks don’t even use “classic” malware: according to the CrowdStrike 2025 report, a full 79% of detected intrusions didn’t use executable malware files, instead relying on “living-off-the-land” techniques such as the use of stolen credentials and legitimate tools already present on the target systems. In practice, cybercriminals often exploit compromised accounts and existing administrative functions to move undetected across networks, evading traditional antivirus programs.
A key role in these silent intrusions is played by info-stealers , malware specialized in stealing credentials and login sessions. In 2025, we observed a massive spread of these tools on the dark web: for example, Lumma Stealer was one of the most prevalent credential theft tools since the beginning of the year. Through stolen credentials (then sold to criminal networks) and inadequately protected RDP/VPN access, cybercriminals can quietly infiltrate infrastructures, bypassing the need to download recognizable malware. Software supply chains have also been exploited: the compromise of third-party updates or libraries has in some cases opened breaches in a number of trusted organizations. These advanced techniques require companies to adopt a proactive security approach, with continuous monitoring for anomalous activity and tight access controls.
Advanced phishing and social engineering

Phishing attacks and, more generally, social engineering scams have reached new levels of sophistication in 2025. Phishing remains the most common initial attack vector, responsible for approximately 60% of the initial breaches analyzed . However, the old, poorly written emails have been replaced by highly convincing campaigns, often powered by generative AI. Industry reports indicate that over 80% of social engineering activities observed in early 2025 involved the use of AI tools. In practice, advanced algorithms are used to craft tailored phishing emails (e.g., fake internal communications or CEO requests) that perfectly mimic the authentic tone and style.
This evolution is manifested in threats like the next-generation Business Email Compromise (BEC) and even audio/video deepfakes . This year, a group of fraudsters successfully tricked a company using a deepfake video of senior executives during a video call, convincing an employee to transfer $25 million. In another thwarted case, criminals spoofed the voice of a well-known company’s CEO to issue fraudulent orders—recognized as fake only by a security question posed by a knowledgeable employee. Large-scale campaigns like that of the Scattered Spider group have also demonstrated the effectiveness of deception: these hackers, suspected of attacks on giants like Allianz, Qantas, Marks & Spencer, and others, excel at impersonating real employees or suppliers to gain access to corporate networks.
Faced with threats like these, which exploit human weaknesses even before technological ones, staff training and ongoing awareness are essential : each individual must learn to recognize the signs of a potential scam (suspicious URLs, unusual requests, urgent requests) and check before clicking . In 2025, this concept has been reinforced: the first line of defense is not antivirus software, but the aware user.
Zero-day vulnerabilities and flash exploits
Another critical threat front in 2025 concerns software vulnerabilities. Hackers have continued to exploit unknown (zero-day) or newly disclosed flaws with impressive speed. It is estimated that over 21% of initial intrusions occur by exploiting vulnerabilities in exposed systems. As soon as a vendor announces a patch for a serious flaw, criminals analyze it and within days launch massive exploit campaigns before organizations can update their systems. This accelerated weaponization has particularly affected widespread Internet-facing applications, such as VPNs and corporate firewalls (such as Citrix NetScaler, Fortinet, Palo Alto), collaboration and ticketing platforms, out-of-date email servers, and so on. One of the lessons of 2025 is that the time between the disclosure of a critical vulnerability and its active exploitation has drastically reduced—in some cases to just days or hours— putting traditional patch management processes under pressure .
There has been no shortage of actual zero-days discovered and weaponized by advanced actors, often with the help of AI. Indeed, artificial intelligence is not merely defensive: as highlighted by the World Economic Forum, criminals are using it to identify unknown weaknesses and develop complex, customized exploits. In 2025, attacks exploited critical flaws in widely used software (e.g., a vulnerability in the popular Oracle E-Business Suite system was exploited by the Clop ransomware, or a flaw in GoAnywhere MFT by the Medusa group). Even known but unresolved vulnerabilities (unpatched systems) have facilitated infections, reminding companies of the importance of maintaining high security hygiene . Overall, these trends underscore the need for a proactive approach: monitoring for new threats, applying timely updates, and perhaps adopting virtual patching and network segmentation to mitigate risks in the meantime.
Attacks on critical infrastructure
 Critical infrastructure ( healthcare, transportation, energy, government agencies) continued to be the target of targeted attacks in 2025, with potential consequences for the community. Hospitals and the healthcare sector in particular have come under intense pressure: cybercriminals know the cost of operational downtime is extremely high (estimated losses of up to $7,900 per minute due to the unavailability of crucial healthcare systems), so ransomware attacks on hospitals provide them with enormous leverage to demand ransom. Unfortunately, several healthcare providers have seen millions of patients’ data exfiltrated. For example, a ransomware attack revealed in 2025 against a major clinic group compromised the personal and medical information of 1.27 million people. Beyond the financial and reputational damage, these incidents pose concrete risks to patient safety and continuity of care.
Critical infrastructure ( healthcare, transportation, energy, government agencies) continued to be the target of targeted attacks in 2025, with potential consequences for the community. Hospitals and the healthcare sector in particular have come under intense pressure: cybercriminals know the cost of operational downtime is extremely high (estimated losses of up to $7,900 per minute due to the unavailability of crucial healthcare systems), so ransomware attacks on hospitals provide them with enormous leverage to demand ransom. Unfortunately, several healthcare providers have seen millions of patients’ data exfiltrated. For example, a ransomware attack revealed in 2025 against a major clinic group compromised the personal and medical information of 1.27 million people. Beyond the financial and reputational damage, these incidents pose concrete risks to patient safety and continuity of care.
The transportation sector has also seen significant incidents: in September, a cyberattack on a shared IT system disrupted check-in counters and baggage carousels at several major European airports, causing delays, cancellations, and widespread disruption. This incident highlighted the interconnectedness of critical services and how a single breach can have international repercussions, requiring collaboration between companies, technology providers, and authorities to restore normalcy. In the energy and utilities sector, vigilance remains high following the incidents of recent years; in 2025, there were several attempted intrusions (both successful and unsuccessful) targeting power grids and industrial facilities, with the intent of sabotage or extortion. Even strategic government agencies have not been spared: the case of a major US nuclear agency being targeted by hackers is a prime example, demonstrating that any organization, no matter how well protected, can become a target.
Faced with these threats, the European Union and other governments are also taking regulatory action. In 2025, new digital resilience regulations (e.g., NIS2 , Cyber Resilience Act, and Digital Operational Resilience Act) came into force in the EU to impose higher security standards, and countries like the United Kingdom are considering a legislative ban on ransom payments by public entities. The goal is to discourage criminals and strengthen the resilience of vital infrastructure.
Impact on data and business, and the importance of backup
The tangible consequences of these threats on the economic fabric and user data in 2025 were significant. Large-scale data breaches exposed millions of people to the theft of sensitive information: in October 2025, for example, nearly all reported major incidents involved data exfiltration (as well as malware or encryption), with millions of users whose personal data ended up for sale on the dark web. These breaches entail extremely high direct and indirect costs for the affected companies: according to an IBM report, the average global cost of a data breach in 2025 was $4.4 million . While slightly lower than the previous year (thanks to improved detection and response capabilities), these figures can still bring an unprepared organization to its knees. Highly regulated sectors such as healthcare also face legal penalties and class-action lawsuits following a compromise, amplifying the long tail of costs for years after the incident. Furthermore, as we have seen, downtime caused by an attack can lead to enormous business losses – just remember the 15 weeks of operational downtime at M&S mentioned above, or the hours of downtime in financial services and e-commerce during some attacks, resulting in lost sales and poor customer service.
Faced with these risks, investing in cyber resilience is crucial for companies of all sizes . This means preventing, but also knowing how to react and recover quickly in the event of an incident. In particular, having up-to-date backups and a robust disaster recovery plan can make the difference between a simple scare and a catastrophe. Having isolated backups allows data to be restored without having to submit to criminals’ ransom demands, preventing both prolonged service disruptions and the permanent loss of key information. It’s no coincidence that Kaspersky experts emphasize that regular backups of critical files are a real lifeline in the event of ransomware , allowing systems to be recovered without paying and without losing data. Good incident response planning (drills, clear procedures, assigned roles) has also proven crucial: companies with incident response teams and tested plans have seen breach costs more than 50% lower than those without. In short, 2025 has taught us that preparation and rapid response are integral to security.
Conclusions and practical advice
2025 has highlighted significant cybersecurity challenges, but it has also reinforced the importance of an integrated approach to cybersecurity . Technology, processes, and people must work together to create robust defenses. For a company in any industry, investing in data protection—through reliable backups, training, and advanced tools—is no longer just good IT practice, but an essential requirement to ensure data security and business continuity in an era of pervasive digital threats. As we look toward 2026, the key word remains resilience : preparing for the worst, hoping for the best, allows us to successfully address even the most critical attack scenarios.
For any questions or doubts regarding this article,
Contact us